Introducing passkey support to Fastmail
Post categories

Chief Product Officer
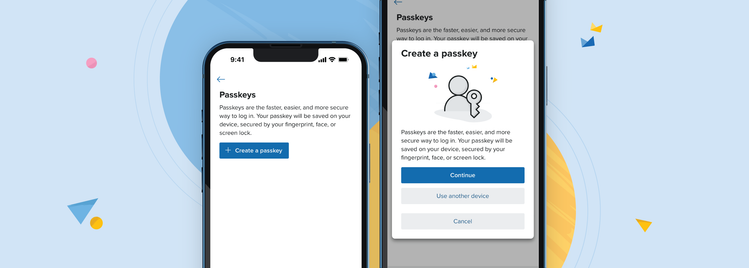
From today, we’re pleased to announce you can create passkeys for your Fastmail account, giving you a faster, more secure way to log in. Open the Privacy & Security settings in your account to get started, or read on to learn more about passkeys.
The problem with passwords
To understand why passkeys are useful, we should start by looking at the problems with passwords that we want to solve.
A password is a shared secret between you and the website you’re logging into. You tell the website who you are (your username/email address) and the secret only you know, the website checks it matches the secret you gave them before, and if it’s a match then you’re logged in.
So far, so good. The trouble is, people are terrible at using passwords.
-
We’re not good at coming up with hard to guess passwords. In security, we have the concept of entropy, which is a mathematical way of calculating how predictable something is. The higher the entropy, the less predictable, and the stronger the security. This is important to stop people from being able to guess your password. Unfortunately, when most people try to come up with a password, they choose something with low entropy, which makes it susceptible to “brute force” attacks, where a computer can try billions of passwords very quickly until it finds which one is yours.
-
We’re not good at remembering lots of different passwords. As we saw above, a truly secure password is something that’s unpredictable. And if it’s unpredictable, it’s probably hard to memorise. Memorising one strong password is probably doable, but using the same password at every site is a terrible idea from a security point of view: all it takes is one website to store its passwords insecurely and a hacker could now access all your accounts, anywhere on the internet!
-
We’re not good at only giving our password to the right website. You may have a phenomenal memory, and maybe roll dice to create a unique password with high entropy for every account you create. Unfortunately, this doesn’t help if you click a link to a phishing website and hand it straight over to an attacker. This is the biggest cause of stolen Fastmail accounts by a long way.
Now, you may be thinking there’s already an answer to the above: password managers. And that’s absolutely right. If there’s one thing you can do to improve your security on the web, it’s use a password manager. A password manager:
- Creates secure, high-entropy passwords for you.
- Remembers them, so you don’t have to.
- Will only automatically fill it in on the website you created the password. (But as autofill isn’t 100% reliable, users can be tricked into manually copying the password out of the manager and into a phishing site).
That mostly solves our problems! But if we’re using a password manager anyway, we can make it even more secure by storing passkeys in it instead of passwords. All modern password managers also support passkeys (there’s a built-in one on every device these days, or we recommend 1Password for a good cross-platform password manager).
What are passkeys, and why are they better than passwords?
Instead of a password - which is a shared secret with the website - a passkey a is a super-secure cryptographic key. It uses public key cryptography, which means your password manager stores a key that can prove it’s you, while the website gets a different key that can only verify this assertion. This has a number of advantages over passwords:
- It’s replay resistant. A password is the same every time, so if an attacker can observe it being sent to the website, they can use it themselves. With passkeys, you sign a different random “challenge” from the website every time, so even if an attacker can intercept your network traffic, they can’t steal your passkey and log in as you.
- It’s database-leak resistant. If a website’s password database gets hacked, there’s a risk the attacker could get your password. (Good websites will have hashed the passwords to slow the attackers down, but it’s still possible.) With passkeys, you have both a private key (that can create a signature to prove it’s you) and a public key (that can only verify the signature is real, but not create it). The website only ever has the public key, so even if this were stolen it couldn’t be used to access your account.
- It’s phishing proof. Passkeys are strongly tied to the website they were created for. If you click a phishing link and end up on a malicious website, your passkey simply won’t appear, so you can’t get phished.
- It’s quicker and easier. Browsers can provide secure, privacy-preserving APIs for integrating passkeys on a website to make logging in as easy as a single click.
Your password manager handles all of this for you. When you want to log in to a website or app, you just use your fingerprint, face, or PIN to verify it’s you (this happens entirely locally - your biometrics never leave your device). The website then receives a digital signature proving you have the passkey, and you’ll be logged in.
How do I log in on a new device?
Your passkey will be stored in your password manager. This will often automatically sync between all your devices. For example, if you use multiple Apple devices, the iCloud keychain will securely sync your passkeys to all of them.
If you don’t have the same password manager available on all your devices, you can also:
- Use the passkey on your phone to log in on another device.
- Create another passkey on the other device to make it easier to log in there going forwards.
You can create as many passkeys for your account as you need; any of them can be used to log in. You can review and revoke the passkeys created for your account at any time from the Privacy & Security settings.
How does this interact with my existing password? What if I have two-step verification?
Passkeys are an additional way to log in, not currently a replacement for passwords. If you create a passkey, you will still be able to log in with your password, just as you did before. If you have two-step verification, this will still be required when you use your password. Two-step verification is not required when you use your passkey, as this already has two factors:
- Something you have (the passkey on your device).
- Something you are or something you know (the touch/fingerprint or PIN your device requires to use it).
The state of passkeys on the web today
We’re a big believer in passkeys, and hope they are the future for authentication. Phishing is a blight on the internet, and this is our best hope of eliminating it forever. We’ve actually had passkeys implemented for over a year at Fastmail, but we’ve been waiting for the ecosystem to mature before releasing it. While it’s come along way, there are still some rough edges.
The biggest issue is the integration of third-party password managers in browsers is still not as polished as it should be. Browser vendors are working on an API for passkey integration but it’s not widely supported yet, so instead the password managers are injecting JavaScript into the page to overwrite the native navigator.credentials object. The result is more fragile - for example, we ran into a bug with 1Password in Firefox, where the getAuthenticatorData method returned an object that throws an error whenever you try to access it, due to extension security controls. It also can result in confusing, competing UIs for the user - the password manager intercepts the calls and presents its own UI, but if you cancel this you might get a browser dialog, which might itself hand over to a system dialog, all with their own style. Integration with the browser’s built-in webauthn support will provide a more seamless experience and allow the user to have passkeys from multiple password managers all available in one place.
Even the native browser APIs can have their quirks, though. For example, Safari requires the webauthn API call to be made in an event directly triggered by the user, like a click. However, the webauthn API requires a challenge, which requires an asynchronous HTTP call to the server to fetch it. So if you trigger this request on the user click, then call the webauthn API with the response, it will fail. Annoying.
The standard for people to export and import passkeys is not yet complete, although it’s getting close. This will allow you to move between password managers without having to recreate your passkeys on every site. Once this is complete and widely adopted it will remove the risk of lock-in, which we believe is currently hampering adoption.
The good news is these problems are all solvable, and the ongoing work shows there is strong industry desire to do so. Despite the current minor issues, we believe the time is now right to start adopting passkeys, and we hope to see their continued success.
